Cybersecurity That Manages Insider and External Threats
LeastTrust specializes in protecting both your client’s data and your valuable in-house data. Cybersecurity tools are not enough. Your organization needs data protection governance, policy, and technology. We can help your firm identify, classify, protect, and track all of your client and in-house data. We leverage tools such as data classification, Data Loss Prevention (DLP), managed browser, external document tracking (steganography), access controls, and forensic logging.
Elite data protection culture does not happen overnight. Strong policies, employment agreements, handbooks, and recurring training are necessary elements that balance deterrent and detective controls. Continuous governance coupled with technology enforcement is the desired strategy to protect your firms data.
Is your data safe?
– Have you recently had an employee exit with proprietary data? Were reasonable protections in place to protect that data?
– Can confidential email and attachments be sent outside of your tracking abilities? How can you verify NDA compliance?
– When is the last time a firm-wide access review has been performed?
– Are you considering turning on Microsoft co-pilot? or another AI addition?
– Do you know where all confidential data resides in your digital landscape from regulated data (PII), client files, evidence, IP filings, and proprietary trade secrets (almost anything in scope)?
– Are some websites off-limits? What about downloads and uploads? Is any online SaaS not permitted?
The good news is that many of these elements including policies, procedures, and training overlap with your current cybersecurity controls.
SOC 2, NY DFS, Cyber Insurance? A data privacy program is a great foundation or augmentation to reach these compliance goals

SOC2
SOC 2 is an audit process that ensures service providers manage data securely, safeguarding your organization and client privacy. For security-focused businesses, SOC 2 compliance is essential when choosing a SaaS provider. Created by the AICPA, SOC 2 sets standards for managing customer data based on five trust service principles: security, availability, processing integrity, confidentiality, and privacy.
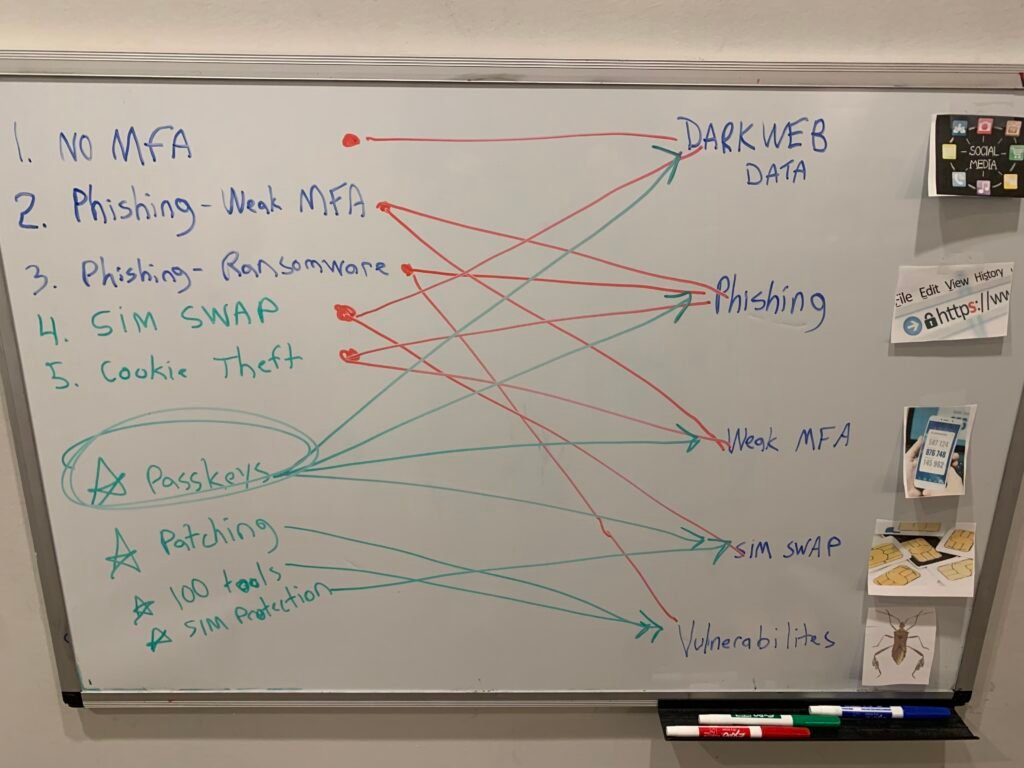
Security Advisory & Awareness Training
- Has your company experienced an incident of data loss, ransomware, or employee theft?
- Are you unsure that your security controls would pass a required compliance audit?
- Are your customers, partners, or investors inquiring to see evidence of reasonable security commitments?
- What is your company’s history in acquiring cybersecurity insurance?
- Ever had an employee exit with customer lists or proprietary data?
These are all common issues incoming clients are facing. Our approach is to understand your business, assess your current security posture, and propose an affordable and viable roadmap to address the gaps necessary to achieve the desired state.
One time, recurring, and flexible partnerships

Data Protection / AI Readiness
Tag, Classify, Protect, Track, and Manage all of your sensitive and proprietary data. We can stand up your data governance

VAULT Cybersecurity Platform
All of the tools, training, and procedures to best protect end clients and individuals. "Investing Only" Laptops.

Vendor Due Diligence | Compliance Readiness | Insurance Readiness
Our mission is to build a sustainable security culture and roadmap. Our VCISO shows the way

Intellectual Property & Insider Threat
It surprising how many proprietary assets are trade secrets. We can help protect them. Patents need to be coupled with know-how (protected trade secrets)
Cybersecurity
Our team hosts cyber awareness sessions for both the community and organizations (NYC Metro and Palm Beach Metro)
Risk & Opportunity Advisory
Lets do an "all hands" whiteboard session.
Are you looking to identify risks or exploit new opportunities?
Agile Transformation
The "Geek" Way and how business disruption is all about working differently
Intellectual Property
All organizations have brand, mission, and IP. Learn how your organization can best protect them.
Client Testimonials