
Step by Step
Regardless of our partnership (Managed IT and/or Cybersecurity) our team regularly meets with your team to listen, design, schedule, execute, and support your organization’s needs.
Requirements gathering (Week 1)
We want to meet all of the team to understand your goals and challenges so our Team can consider the ideal IT, sensitive data, internal privilege holders, and additional integrations. We do not bill for requirements gathering. The more depth and understanding that is conveyed the clearer expectations will be. This is the foundation for a successful partnership.

Architecture & Proposal (Week 1-4)
The next step is architecting a roadmap of tools, services, schedule, risk register, and performance metrics.
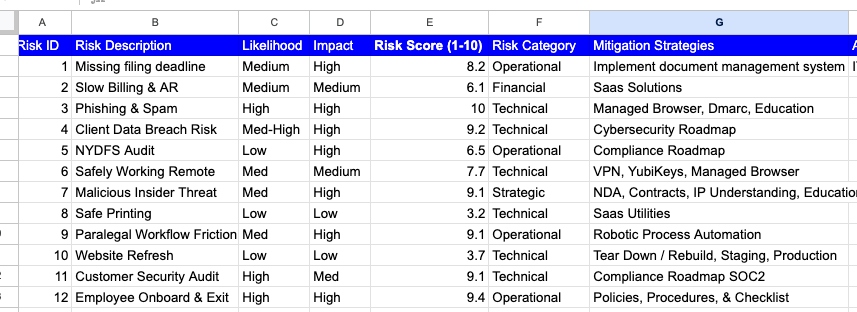
Kickoff (Week 2-4)
Once approved, the IT or Cybersecurity plans are kicked off. Cybersecurity may include a risk assessment, regular security awareness education, tool training, policy creation/review, and compliance documentation improvement

Improvement Cadence (Continuous)
Steady improvement requires consistent communication, metrics reviews, and emerging risk/opportunity analysis.
Nationwide Coverage
Our Team is located across the United States and can respond to your needs virtually in real time or be on location in hours.




