Cybersecurity Roadmaps
What is your Organization’s Security Destination?
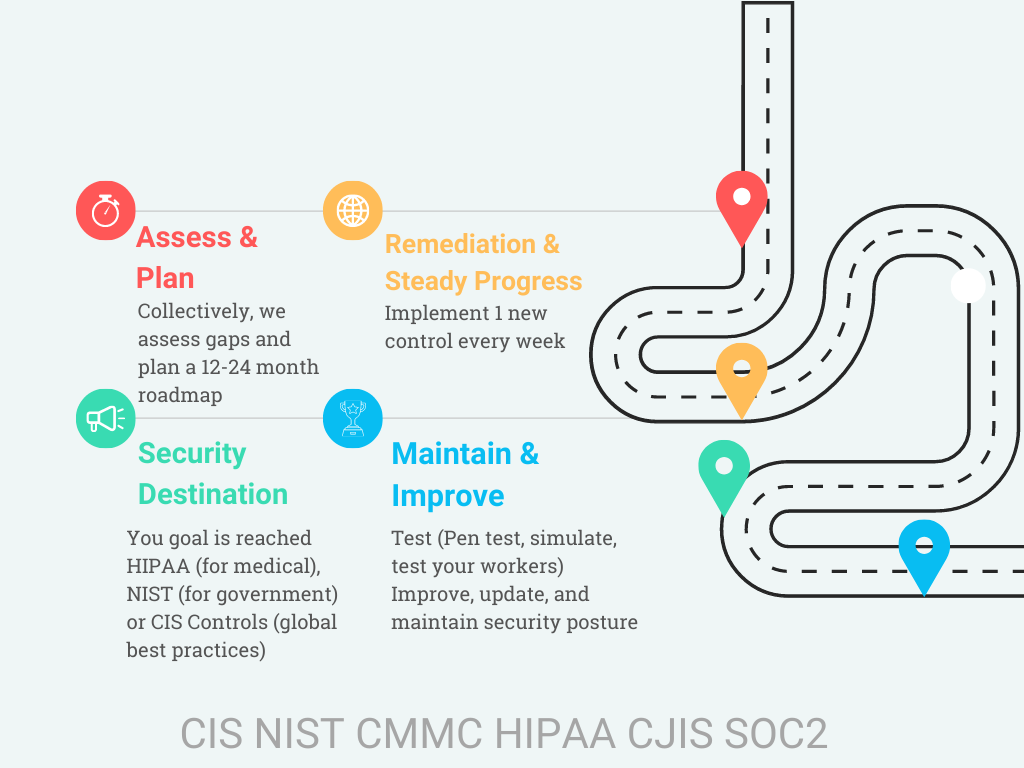
Day 1 : Assess & Plan
Your organization decides what security destination or roadmap is ideal. Do you want to implement 150 CIS controls over 2 months or 2 years? We can plan for that. How about HIPAA compliance? or another regulation like FTC? We have you covered. Our security roadmaps (often called Compliance as a Service) is a integral part of offering secure IT.
NYDFS Cybersecurity requirements PDF
Weekly Progress
LeastTrust IT will share a planning platform with your organization that will guide, schedule, task, and document all of your control implementations. The standard cadence is 1 control implementation per week. Your organizations security posture gradually progress week by week as will your security culture.

Continuous Testing & Improvement
Once you reach your desired security destination, you can choose to test your controls effectiveness with an external audit, a penetration test and/or simulation. Going forward, controls will be updated with changing best practices, and reviewed on a recurring basis to make sure controls remain effective.
FAQ
What is a VCISO?
VCISO – virtual or fractional CISO (Chief Information Security Officer) is a external advisor that helps quantify risks and opportunities to an organization. Business objectives are aligned with cybersecurity efforts and the value of resilience is core to the program roadmap. Typically the engagement starts with a gap assessment, conversation of scope, and continues into risk remediation and control deployments alongside the company personnel. Long term retainers are possible and recommended to continue the maturation of the program.
Can LeastTrust help a company attract investment?
LeastTrust IT strives to increase the value of its clients by integrating and evidencing strong cybersecurity and Intellectual Property (IP) systems. Additionally the ability to evidence security can aid in client 3rd party due diligence, suppliers, partners, and insurance relationships.
What about additional security tools?
LeastTrust IT has a range of relationships both directly and with channel distributors of cybersecurity tools. Ideally the billing relationship is directly with the vendor and our team helps integrate and optimize the technology for your goals.
Why does LeastTrust IT Recommend CIS Controls
The CIS (Center for Internet Security) organization is a grass roots global effort of public, private, and military cybersecurity volunteers working together to produce best practices for running a security program. NIST, SOC2, and others often refer to CIS controls. Every few years, the standards are updated based on recent global breach data and a healthy debate from its security volunteers. CIS Controls have the fewest conflicts or interest and are a great example of cybersecurity defenders collaborating to create a better playbook for security.
What are MSPs?
MSP Stands for Managed Service Provider. MSPs are IT outsourcing firms for small and medium sized businesses. Although LeastTrust IT may be considered an MSP we differentiate ourselves by focusing specifically on data privacy, IP, security compliance and roadmapping. We frequently partner with MSPs to assist with either governance or risk functions
What is an MSSP?
MSSP stands for Managed Security Service Providers. MSSPs can vary greatly in their service offerings, but largely offer SOC (Security Operations Centers) and 24/7 incident response. They monitor tools like SIEM (Security information event management) and EDR (End Point Detection). Their is a bias toward MSSPs focusing on detection and response, Although LeastTrust IT is focused on “security first”, our company is unlikely to be labeled as an MSSP.
Should we use an MSP, MSSP, and VCISO at the same time
Although the services may overlap, each of the providers MSP (IT and helpdesk), MSSP (usually cyber incident response), VCISO (building cyber defenses), is common for small and medium sized businesses. Least Trust has deep relationships with each and can recommend criteria to evaluate them.
Can LeastTrust audit our financial documents
LeastTrust IT cannot audit your organizations security program because we believe we need to maintain independence and a 3rd party audit would be applicable to validate the implementation and current state of controls.
You Want an IT Provider that will build a security culture, not re-sell you tools
Come see how LeastTrust IT is different

