Cybersecurity, IP, and Insider Threat Advisory
Inquisitive IT delivers organizations and individuals the same IT, cybersecurity, risk & governance approach that large organizations deploy. How do we make it affordable? Our core strategy is called Least Trust Lean Function. The strategy is to provide employees the right amount of data access while also the ideal amount of IT resources. The “right amount of IT” without bloat and focus on business outcomes is the best strategy to achieve resilience. Additionally we use best in class authentication to defend against the majority of the common attacks published in the Verizon Annual Breach Report. Our strategy and supporting documentation is one that regulators, auditors, and outside stakeholders want to hear. We may also assist your end clients by providing tools, procedures, and education to protect their account access and assets in them. We call this secure laptop our VaultBook. To the user its simple to use. To cyber practitioners this laptop relies on physical encryption keys, privacy configurations, and selected CIS Chrome Recommendations.
The majority of our new businesses and individuals utilize Google Workspace as it is cheaper and simpler to secure than the status quo (and aligns with our Least Trust Lean Function strategy). Workspace can be delivered via a managed browser or via Chromebook. We also assist Microsoft clients with building compliant cybersecurity programs. Inquisitive IT deploys over 100 CIS (Center for Internet Security) controls for each organization it manages while also providing all clients access to a Virtual Chief Information Security Officer (VCISO). Cybersecurity programs require people, processes, and technology. Stop renting a set of tools and come see how Inquisitive IT is different. Let’s tie your business goals to an effective IT strategy.



Why Google?
Our team consists of cybersecurity practitioners, business founders, financial analysts, and technology engineers. We have deep experience securing and optimizing Google Workspaces (formerly G Suite).
Google Workspaces dramatically reduces the attack surface by using browser based utilities and built-in security features such as Single Sign-On (SSO), password-less encrypted passkeys, dual authentication, access logging, and a managed browser. This architecture makes it more affordable to secure, less tedious for your team, and tougher for hackers to get in. Workspaces allows your team to securely work anywhere. All of the utilities of a traditional desktop including spreadsheets, custom email, storage, backup, workbooks, calendar, MDM (mobile device management), access logging, and telephony are built into one integrated office system. Come check out how easy business can be on Google.
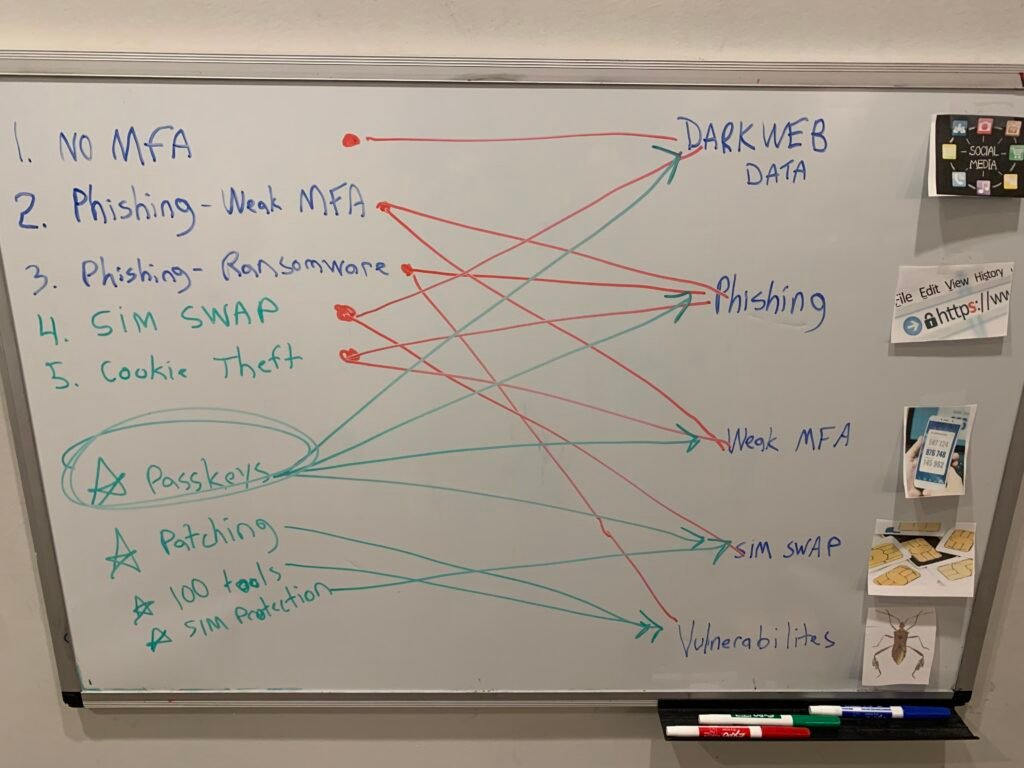
Security Advisory
- Has your company experienced an incident of data loss, ransomware, or employee theft?
- Are you unsure that your security controls would pass the necessary compliance audit?
- Are your customers, partners, or investors inquiring to see evidence of reasonable security commitments?
- What is your company’s history in acquiring cybersecurity insurance?
- Ever had an employee exit with customer lists or proprietary data?
These are all common issues our clients are facing. Our approach is to assess your current security posture and propose an affordable and viable roadmap to address the gaps necessary to met the required target.
Our Services
One time, recurring, and flexible partnerships

Cybersecurity Vault Platform & training for Individuals
All of the tools, training, and procedures to best protect end clients and individuals

Risk Assessment & Compliance Readiness
Our mission is to build a sustainable security culture and roadmap. Our VCISO shows the way

Managed security & IT
Our goal is to secure and manage your IT so that you can run your business or affairs without disruption

Intellectual Property & Insider Threat
It surprising how many proprietary assets are trade secrets. We can help protect them
Inquisitive IT
Cybersecurity
Secure IT (& the Evidence to Support it)
Risk Advisory
Risk & Governance (Including Policy Recommendations)
Compliance
HIPAA, GPDR, GLBA, SEC, SOC2, ISO
Intellectual Property
Identify, Protect, Exploit
Client Testimonials

Nationwide Coverage
Our Team is located across the United States and can respond to your needs virtually in real time or be on location in hours.